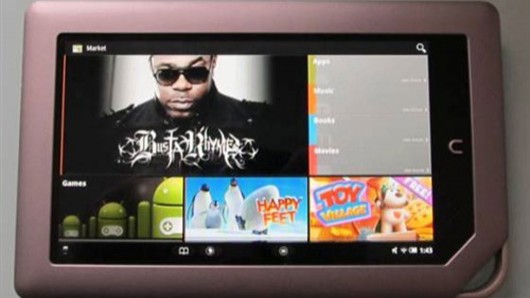
By Eric Mack Rooting the Nook Tablet expands the slate’s horizons with the addition of the Android Market The Nook Tablet from Barnes and Noble offers meatier specs than Amazon’s Kindle Fire for half the price of an iPad, but the selection of apps on offer for the e-Reader/tablet hybrid is a bit underwhelming. Fortunately, […]

By the Editors Dec 15, 2011 5:00 PM MT Chinese hackers have redefined the concept of room service: In one recent attack, they infiltrated an Internet service provider to some of the world’s leading hotels, potentially gaining access to millions of confidential messages of traveling executives, as well as to the victims’ corporate networks. The electronic theft of proprietary information […]
Published 14 December, 2011 – 07:20 In a recently released report, researchers from the Massachusetts Institute of Technology say that a single federal agency should be tasked with protecting the United States’ electrical grid from cyberattacks; the Obama administration has proposed that DHS assume responsibility for the grid, while Congress has submitted proposals for both […]
Documents point to a huge industry that provides online surveillance tools to governments and police agencies. By David Talbot A claim by Wikileaks that documents it released last week provide evidence of a “secret new industry” of mass surveillance was as breathless as previous pronouncements from Julian Assange’s organization. But the material does provide a stark reminder […]
Hackers are learning new lessons from the most sophisticated virus code ever written BY STEVEN CHERRY // WED, DECEMBER 14, 2011 Last year, we did a show about the Stuxnet worm that was one of the most listened to of the year. In fact, it’s one of the most listened-to shows of this year as well. Last week, […]
In an unprecedented move, for the next three months the Los Angeles Police Department (LAPD) will rely entirely on computer software to decide where to deploy patrol officers; the predictive analytics software examines data from past crimes to determine when and where certain crimes are likely to occur next so police can be on […]
By Jim Finkle Sat Nov 19, 2011 2:05am EST (Reuters) – Federal investigators are looking into a report that hackers managed to remotely shut down a utility’s water pump in central Illinois last week, in what could be the first known foreign cyber attack on a U.S. industrial system. The November 8 incident was described in […]

At the recent Hackers Halted convention in Miami, researchers John J. Strauchs and his daughter Tiffany Strauchs Rad told the audience how with only $2,500 and some basic equipment, they were able to develop a cyberattack on a simulated prison computer system with potentially catastrophic results Research into possible weaknesses in the U.S. prison system’s […]
By Derek Top HP unveiled a plan for new, low-energy server technology and launched a hyperscale business unit committed to data center efficiencies. The program, dubbed Project Moonshot, includes a server computing design intended for high-volume, large-scale data environments — such as those found in web- and cloud-based applications — and could reduce energy requirements by up […]

By Jim Finkle Mon Oct 31, 2011 5:38pm EDT (Reuters) – At least 48 chemical and defense companies were victims of a coordinated cyber attack that has been traced to a man in China, according to a new report from security firm Symantec Corp. Computers belonging to these companies were infected with malicious software known as “PoisonIvy,” […]